POC WCH CTF
WHITEHATCREW CTF 2022
Writeups for CTF
Category : Cryptography
1.Beginner Cryptograph
- First, we will get a code like this =[ YmFzZTY0X2lzX292ZXJyYXRlZA== ]
- Then, we decode it to base64 -[ base64_is_overrated]
- The answer will be WCH{base64_is_overrated}
2.Anencephaly
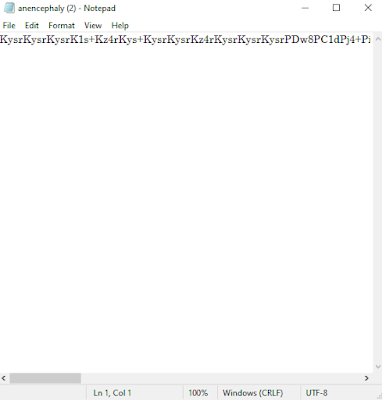
- First, we will get a file name anencephaly
- There is a code inside it
- Decode it to base64 and we will get :
- And we will get a new code : [V0hDe0FQQV9LQUlUQU5fRE99]
- Decode it to base64 and get the answer = WHC{APA_KAITAN_DO}
3.Botak
- First, we get a pyhton coding
- Open it with IDLE and there is comment with a code
- Run the python coding that given and use cipher decoder to get the answer
- Then we will get the answer = WCH{unclePenatLahSiapaBuatNiMemangNakKenaPukul}
4.XORing
- We will get a zip file name XORing.7z
- Inside it there is some clue:-
- The key need to change into ascii value and we will get the key is actually = [\r]
- I used https://www.101computing.net/xor-encryption-algorithm/ to solve it
- The answer is Cipher (Ascii form): WHC{X0R40BFUSC4T10N}
Category : FORENSIC
1.Beginner Forensics
- We get a file named set1.pcap
- Open it using wireshark and search for readable text
- So the answer will be = WCH{5:What, me worry?}
2.1 Penceroboh-1
- We will get zip file name Penceroboh.7z
- Inside there is penceroboh.pcap, open it in wireshark
- And search for readable text, we will found three different user
- Find Authorization: basic [user and pass] and decode to base64
- For now we need to search user start with A letter
- The answer will be = WCH{aoursler:Id10tExpert}
2.2 Penceroboh-2
- Search another user starts with B letter
- The answer will be = WCH{brodgers:TheyPlayedWithGreatCharacter}
2.3 Penceroboh-3
- Search the last user
- The answer will be =WCH{dmoyes:IAmAFootballGenius}
3. Topi Putih
- First, we will get zip file name topiputih.7z
- Extract and we will see a white hat picture
- Open it in notepad and you will get the answer =WHC{wh1t3_h4t_cr3w!}
Category : MALWARE
1.1 Malware A-1
- First, we get a zip file name Infected.7z
- Extract and open it using virustotal
- Look at detail: Basics properties: SHA-256
- And we will get the answer = WCH{ba47f657a4745c96a62c444100d6c38bbff772b47ac03e83dc3ef5d94bc1d77c}
1.2 Malware A-2
- At virustotal too we can get the answer
- The answer will be = WCH{BitRAT|185.244.30.28|mal100.troj.evad.winEXE@14/11@0/1}
1.3 Malware A-3
- Open joesandbox link analysis joesandbox
- And use sample name for the answer
- So the answer will be = WCH{0kEuVjiCbh.exe}
1.4 Malware A-4
- Also look on joesandbox analysis
- Search for icon hash
- The answer will be = WCH{f14cd6920f4d8ed4}
1.5 Malware A-5
- Open threatfox.abuse
- search for oic:185.244.30.28(host)
- And we get the answer
- The answer will be = WCH{161038|botnet.cc}
2 Malware B-1
- First , we will get zip file name infected-2.7z
- Extract it and open in virustotal
- Search for dropped file
- Then we will get the answer =WCH{services.exe:bf316f51d0c345d61eaee3940791b64e81f676e3bca42bad61073227bee6653c}
3.1 Malware D-1
- Same process like before, extract and open in virustotal
- Search for the SHA256
- So the answer will be =WHC{bfe041c715d002fb780c6a359080dbe2e711fc1808785f22fbed1d524fb761e8}
3.2 Malware D-2
- If there is no dropped file we can use execution parents
- So the answer will be = WCH{125acc541a506336ba47892211c91e472d94f9160fbcf5ed6b364cbc67f4b410}
3.3 Malware D-3
- Search at behavior
- Then we will get the answer
- So the answer will be = WCH{SE_LOAD_DRIVER_PRIVILEGE}
4. Adventure time
- Open the file
- Go to bin
- open the adventure time.bat
- There we will get the answer = WHC{FUN_PR4NKS_L0NG_AG0}









































Comments
Post a Comment